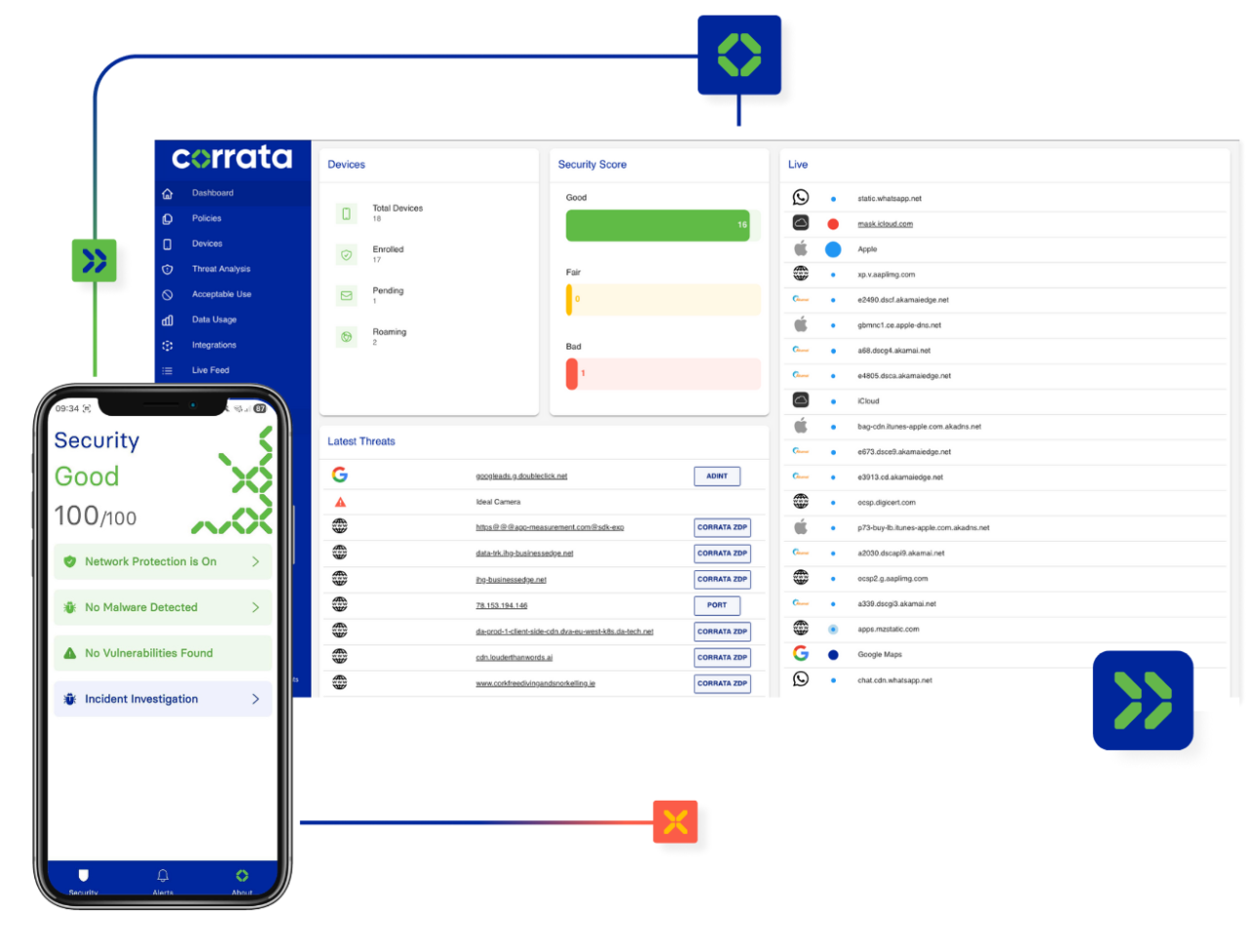
Threat Detection and Response for Mobile
See every mobile threat. Stop it instantly. Protect users without slowing them down. EDR and DLP for mobile endpoints, deployed in 24 hours or less – with no friction and no compromise.
Trusted by
Why Corrata?
A unique on-device architecture proven to deliver superior threat mitigation and to better protect sensitive data, to work unobtrusively on your employees’ devices and to resolve issues without escalation.
the % of threats Corrata detects that others miss

Modern Day DLP: Navigating AI & Off-Channel Risks

Detecting and Mitigating Mobile Spyware
Stop cyberattacks, prevent data loss
For any organisation that wants to secure their mobile endpoints and prevent data loss, Corrata offers cutting edge protection that goes beyond the current state of the art.
Mobile Phishing Protection
Every day employees are being targeted with mobile phishing attacks which leverage SMS, QR codes, messaging apps and social media to harvest credentials, steal authentication cookies and more.
Learn moreSpyware Detection
Sophisticated spyware such Pegasus, Graphite and Predator is used to undermine the built-in security of both iOS and Android, making your organization's most sensitive communications accessible to bad actors.
Learn moreData Loss Prevention
With the rapid growth in ShadowAI the risk that sensitive data will be uploaded to unsafe applications has never been higher. Data leakage through the online advertising ecosystem is another urgent and other overlooked risk.
Learn moreDevice Trust
It's critical that any device your employees use to access enterprise applications is secure. Having a robust way to achieve device trust for both corporate and personally owned devices is essential.
Learn moreVulnerability Management
Good device security posture is critical to reducing risk. Corrata monitors the settings and activity on your employees’ devices, assessing their security status and prompting end users to remedy any issues found.
Learn moreAiTM Protection
In today’s cloud-centric world most enterprise data travels over networks which are fundamentally insecure. Corrata provides the protection you need to ensure that your data remains private.
Learn more
Review
Corrata delivers full visibility over the threats targeting our employees’ mobile devices, instantaneously blocking malicious content, quarantining insecure devices and protecting us from malware. We find the solution is easy to deploy, requires little ongoing effort and delivers a great end-user experience.
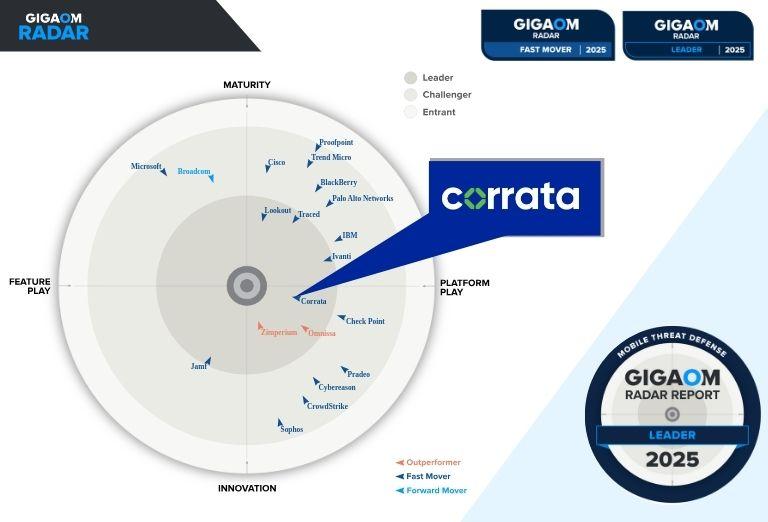
Research Reports and Whitepapers
See how Corrata stacks up against its competition in independent reports and access Corrata’s insights on critical topics in mobile security.
Corrata
"The real-time threat defense without requiring a VPN tunnel is what stands out the most."

Gartner® and Peer Insights ™ are trademarks of Gartner, Inc. and/or its affiliates. All rights reserved. Gartner Peer Insights content consists of the opinions of individual end users based on their own experiences, and should not be construed as statements of fact, nor do they represent the views of Gartner or its affiliates. Gartner does not endorse any vendor, product or service depicted in this content nor makes any warranties, expressed or implied, with respect to this content, about its accuracy or completeness, including any warranties of merchantability or fitness for a particular purpose
Corrata
"Corrata provides a strong balance of mobile security and usability. The deployment was straightforward, and ongoing management is simple through their admin console."

Gartner® and Peer Insights ™ are trademarks of Gartner, Inc. and/or its affiliates. All rights reserved. Gartner Peer Insights content consists of the opinions of individual end users based on their own experiences, and should not be construed as statements of fact, nor do they represent the views of Gartner or its affiliates. Gartner does not endorse any vendor, product or service depicted in this content nor makes any warranties, expressed or implied, with respect to this content, about its accuracy or completeness, including any warranties of merchantability or fitness for a particular purpose
Ready to protect your business?
Corrata offers the most advanced protection available. See the difference it can make today.